A team of researchers presents the first proof-of-principle demonstration of an agile and versatile quantum communication system, using signatures and secret sharing protocols in the same hardware sender and receiver platform.
As the advances in several fields of knowledge - such as mathematics or computing - threaten the safety of our digital infrastructure, researchers around the globe have been developing, testing, and improving new algorithms and cryptographic methods to avoid information breaching. Unfortunately, this process is costly and takes time. Agile cryptography and versatile cryptography have arisen as promising solutions to this issue.
On the one hand, agile cryptography allows swapping efficiently between systems when the security of an algorithm is compromised, adding a two-way interface layer between the software application and the algorithm. On the other hand, versatile cryptography allows users to switch cryptographic tasks without requiring knowledge on how the system works from the inside.
Now, as part of the Quantum Flagship’s projects PhoG and CiviQ, researchers from the Max Planck Institute for the Science of Light in Germany and the University of St. Andrews in the United Kingdom, have applied these cryptographic principles to quantum communication. In their work, published in the journal Physical Review X, the team has defined the concepts of quantum crypto-agility and quantum crypto-versatility by showing a layer-based description of a cryptosystem, and how its modular components can be moved around and recombined similar to the pieces of a puzzle.
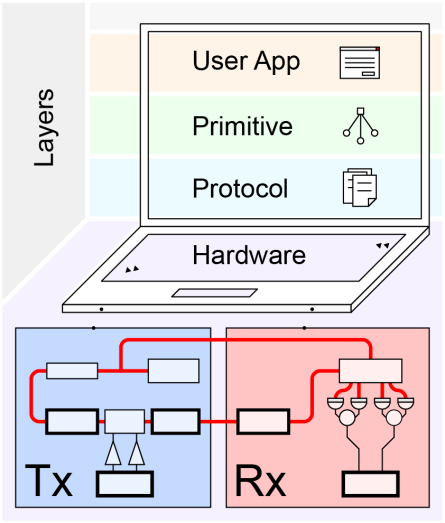
A schematic drawing indicates the different abstraction layers of quantum crypto agility and versatility. Those layers are realized in the demo system as different pieces of software running on a laptop, connected to the sender (Tx) and receiver (Rx) hardware. The Tx and Rx modules used to perform the four distinct quantum protocols.
In their study, they argued that a quantum system is can be agile when the deployment of the different cryptographic capabilities is done in a stable and opaque interface to the end-user, so any change that is made is done at the middleware level without changing the user software. In addition, the system is said to be versatile if it allows switching between cryptographic tasks without requiring the user to have any sort of knowledge on how the system works. This switching also happens at the middleware level. By adding a middleware, a two-way interface layer between the software application and the algorithm, the system can select the suitable quantum crypto primitives and hardware compatible protocols to fulfill a given user request for a given cryptographic task.
In their study, the researchers presented the prototype of a flexible continuous-variable (CV) quantum communication system. Like today’s ubiquitous network interface cards (NICs), a hardware component that connects a computer to a computer network, similar systems could be integrated as ‘Quantum-NICs’ or QNICs in the computers of tomorrow. By using a CV-based system, they tested three protocols; quantum key distribution (QKD), quantum digital signatures (QDS), and quantum secret sharing (QSS). The first one allows encrypting a message safely. The second, to securely authenticate a message. And the third, to securely distribute a secret among potentially dishonest recipients.
For the demonstrations, the team used their continuous-variable (CV) quantum communication system built almost entirely from commercial telecom components, operated at a sending rate of 1GHz. That makes the system compatible with currently deployed infrastructures and with the capacity of high sending rates.
The proof-of-principle test demonstrated versatility by showing that, no matter which protocol they ran, they could use the same quantum sender and receiver performing several tasks in the same system. When potentially vulnerable, they argued that the crypto-core, encryption, and security library, can be replaced without affecting the whole system, because there is an abstraction layer, the middleware, between the quantum hardware and the post-processing stack that allows doing this quite easily. So, the inner workings of the task remained opaque to the user, implying agility by enabling their implementation to be changed even after deployment.
Cited article
Stefan Richter, Matthew Thornton, Imran Khan, Hamish Scott, Kevin Jaksch, Ulrich Vogl, Birgit Stiller, Gerd Leuchs, Christoph Marquardt, and Natalia Korolkova. Agile and Versatile Quantum Communication: Signatures and Secrets. Phys. Rev. X 11, 011038.



